Fortify Your IT Infrastructure
24x7 Security Operations Center to Prevent Cyber Threats
What is a Security Operations Center (SOC)?
A Security Operations Center (SOC) is an essential facility within any organization that prioritizes cybersecurity and the safety of its digital infrastructure. Operating around the clock, the SOC is designed to proactively monitor, prevent, detect, investigate, and respond to potential cyber threats. This continuous vigilance ensures that any security incidents are addressed swiftly and effectively, minimizing potential risks and damages.
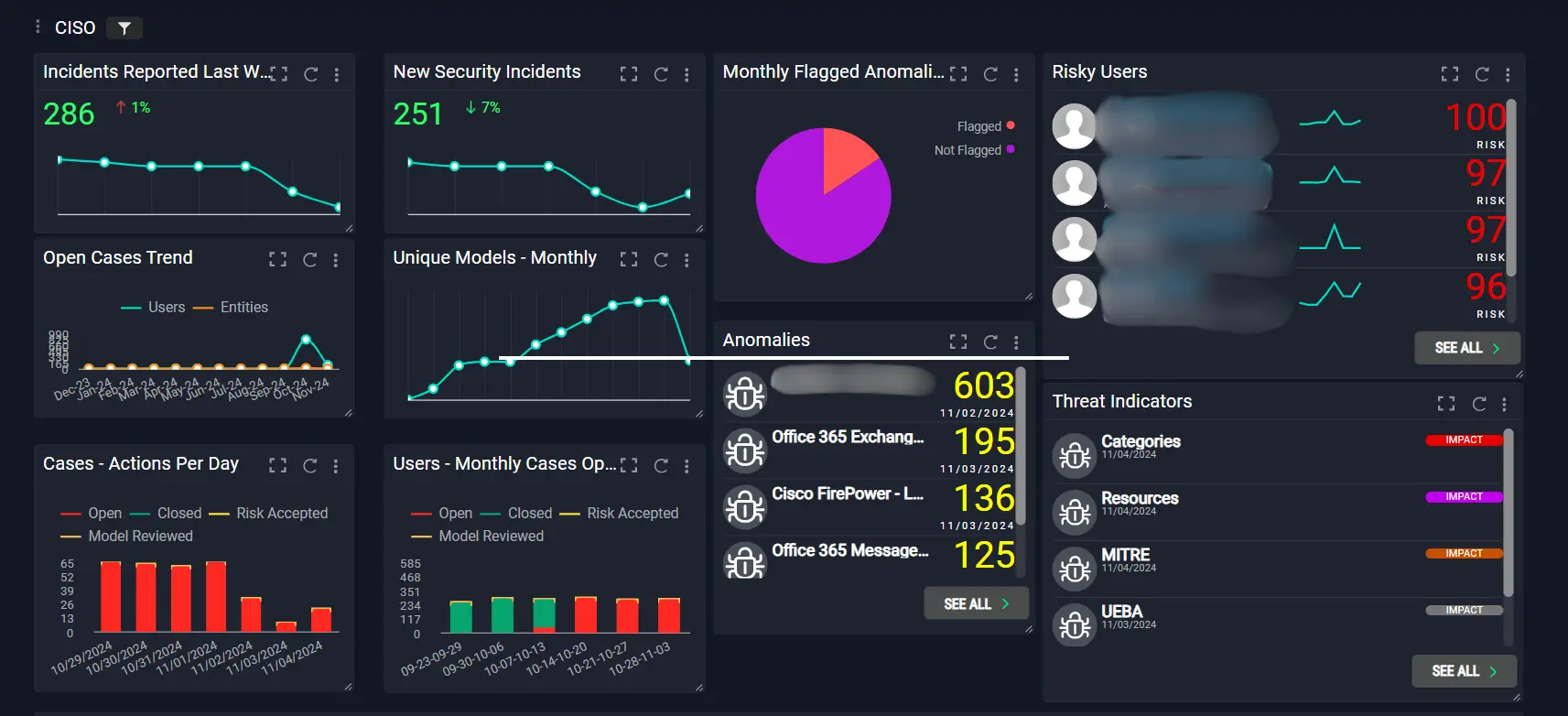
Core Functions of a Security Operations Center (SOC)
Monitoring
The SOC’s primary role involves continuous, around-the-clock monitoring of the organization’s network to ensure constant vigilance over potential security threats. This ongoing surveillance is crucial for the early detection of unusual activities that could signify security breaches. By maintaining an unwavering watch over the network, the SOC ensures that the organization’s cybersecurity posture is proactive rather than merely reactive.
Show MorePrevention
In cybersecurity, the principle that prevention is better than cure holds paramount importance. The SOC implements robust security measures designed to prevent unauthorized access and potential threats before they compromise the network. This proactive stance involves deploying advanced security protocols, maintaining up-to-date defense systems, and ensuring all organizational assets are shielded against emerging threats.
Show MoreDetection
Detection involves the identification of potential security threats as soon as they manifest. SOC teams use sophisticated tools and technologies to recognize signs of malicious activity. When something suspicious is detected, it triggers an alert, prompting SOC analysts to swiftly gather detailed information and prepare for a thorough investigation. This quick detection is vital for minimizing the potential impact of security threats.
Show MoreInvestigation
Once a potential threat is detected, SOC analysts conduct a comprehensive investigation to determine the nature of the threat and assess how deeply it has penetrated the organization's infrastructure. Analysts employ a strategic approach by examining the network and operations from an attacker's perspective, identifying vulnerabilities and indicators of compromise. This stage combines in-depth knowledge of the organization's systems with the latest in global threat intelligence, informing the SOC team about attacker tools, techniques, and tactics.
Show MoreResponse
Following the investigation, the SOC team coordinates a swift and effective response to mitigate and remediate the issue. Immediate actions may include isolating infected endpoints, terminating malicious processes, and deleting corrupted files to prevent further damage. In the aftermath of an incident, the team focuses on system restoration and data recovery, which may involve resetting systems, applying necessary patches, and deploying backups to restore operational integrity.
Show MoreWhat is SIEM and its Contribution to SOC Operations?
SIEM (Security Information and Event Management) technology is pivotal in the realm of cybersecurity, especially within Security Operations Centers (SOCs). It acts as a sophisticated framework that gathers, normalizes, and analyzes extensive security data from a myriad of sources across an organization’s IT infrastructure. This includes data from network devices, servers, databases, and applications, thereby providing a holistic view of the security landscape.

Benefits of SIEM in SOC
By integrating SIEM into SOC operations, organizations significantly bolster their cybersecurity defenses, ensuring a proactive stance against threats and a comprehensive strategy for incident management and compliance.
Enhanced Threat Detection : SIEM systems aggregate and correlate data across sources, boosting the SOC team's ability to detect advanced threats. This analysis reveals subtle anomalies and patterns that indicate security breaches.
Real-Time Monitoring and Visualization : SIEM provides immediate insights into security events through real-time processing and intuitive dashboards, allowing for quick identification and resolution of anomalies.
Streamlined Incident Response : SIEM prioritizes alerts to enhance incident management, enabling SOC analysts to swiftly address the most critical threats and optimize resource allocation.
Regulatory Compliance and Forensic Analysis : SIEM supports compliance by securely logging and archiving security data, which is vital for compliance audits and forensic analysis post-security incidents, offering insights into attack patterns and vulnerabilities.
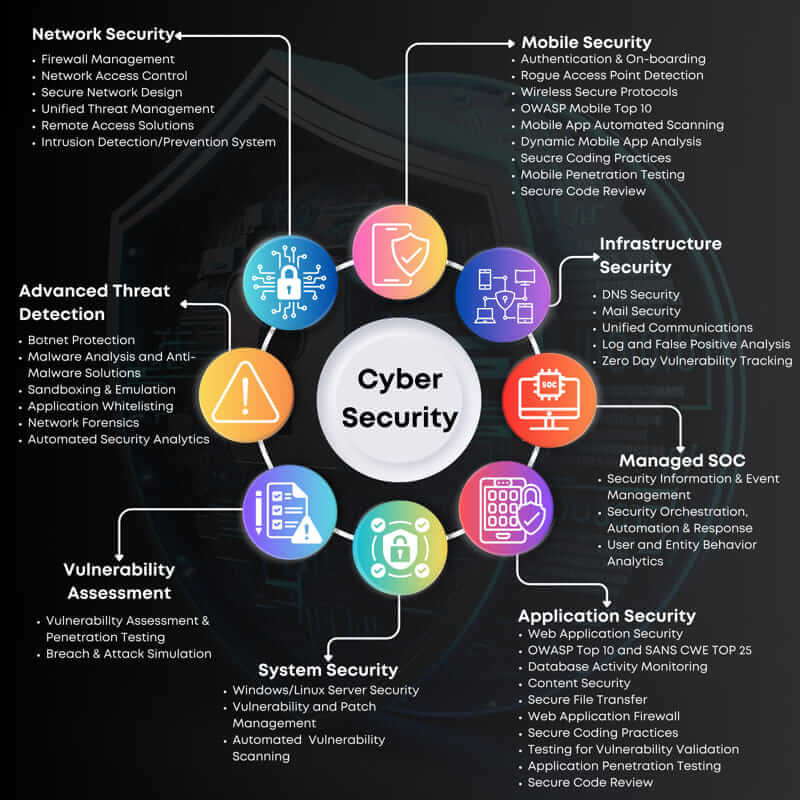
Advanced Security Technologies: UEBA, SOAR, and OT Security
Enhancing Cybersecurity with UEBA (User and Entity Behavior Analytics)
UEBA technology represents a significant advancement in cybersecurity, focusing on detecting anomalous behavior and potential threats. By analyzing the actions of users and entities across the network, UEBA helps identify unusual patterns that may indicate compromised credentials, insider threats, or external attacks. This proactive detection is essential for mitigating risks before they escalate into major breaches.

Streamlining Responses with SOAR (Security Orchestration, Automation, and Response)
Incorporating SOAR solutions enhances the efficiency and effectiveness of security operations. By automating routine tasks and orchestrating complex processes across various security tools, SOAR significantly reduces the time it takes to respond to incidents. Customizable playbooks ensure that every alert is handled according to a predefined workflow, thereby standardizing response strategies and minimizing human error.

Safeguarding Critical Infrastructure with OT Security (Operational Technology Security)
As operational technologies in critical infrastructures like manufacturing plants, utility facilities, and transport networks become increasingly interconnected with IT systems, the need for robust OT security becomes paramount. OT security strategies are designed to protect these systems from both cyber and physical threats, ensuring the safety and reliability of essential services. Implementing stringent cybersecurity measures along with rigorous physical controls helps shield these vital systems from disruptions.

The Security Gap
Product V/S Use-case
Security technology investment is primarily product/OEM driven rather than use case driven
Great Resignation
The need to build resilience into security talent pool amid the great resignation wave
Alert Fatigue
Coping up with a near-constant barrage of alerts and complex security incident and event management (SIEM) tools
Low Perceptive ROI
Cybersecurity confidence rattled by continued investments, but with negligible to no results
Lack of visibility to identify genuine threats for risk management
- Lack of visibility to identify genuine risk
- Perpetually changing threat landscape
- Inefficient IT security budget allocation
- Complexity in regulatory compliance
- Hard to find cybersecurity expertise
- Unaware employees & insider threats

Rethink Your IT Security
Major Milestones
- Installing and Integrating Telemetry
- Writing Correlation Rules
- Laying down processes - Incident management, change management etc.
- Steady state is all about generating Monitoring dashboard, Alerts and Reports
Challenges
- Focus remains on Log collection and Security takes the backstage
- Majorly ‘Out-of-the-box’ rules, difficult to test in the real environment
- Manual processes, Loosely defined Playbook/Runbooks
- Cyber landscape changes every day, and so should SOC
Major Milestones
- Well-defined security strategy and use cases
- Mapping the use cases with Telemetry (Understanding the difference between Forensics and Active Monitoring)
- Using API Framework for proper Playbook and Runbook Integration
- Simulation Based Operations
Advantages
- Clarity on what are we going after
- Use-Case based Telemetry selection
- Putting existing investments into their best use
- Continuously Improving and updating the SOC
Improve Your Organization’s Security Posture
CISO Assist
- Risk Assessment
- Security Policy Development
- Incident Response Planning
- Cyber SOC-BOT Model
- Cyber Workforce Development
Cyber Intelligence Center
- VAPT
- Cyber Monitoring Services
- Cyber Remediation & Management
- Threat hunting Services
- Security Automation
- OT Security
- Breach Attack & Stimulation
Our Cyber Security Management Capabilities
Threat Hunting
Behavior analytics, Incident response and Breach response
Breachability Score
24X7 vulnerability & Configuration watch
Threat Intel Engineering Service
Open-Source Intelligence, Dark & Deep web Intelligence, Multi Vendor feeds
Detection Service
Custom use-case based Correlation. & IOC, Attack Pivots, Lateral movements, UEBA monitoring
Response Automation
Security Orchestration and Automation Response
Attack Simulation & Training
Attack Simulation & Response Testing. Cybersecurity Trainings.
Hunting
Recon & Detect
Managed Incident Response
Alerting
Reporting
Advisories
24x7 Event Monitoring Services
Access Profile
Threat Profile
24x7 Device Managed Services
SOC Engineering Services | Threat Use-Cases Definition | Log Engineering Framework
Comprehensive Cybersecurity Suite: Keeping Your Digital World Safe
In an increasingly interconnected world, cybersecurity is paramount, Our comprehensive cybersecurity suite offers a range of services designed to protect your digital assets from evolving threats. From proactive threat detection to real-time incident response, our suite is tailored to meet your organization's unique security needs. Our team of seasoned experts stands guard, ensuring your data is fortified and your operations remain uninterrupted.
With our cybersecurity suite, you're not just protected – you're empowered. Focus on growth and innovation while we secure your digital fortress, ensuring your peace of mind in an ever-changing digital world.
Delivering Outcomes for a Secure IT Environment
Services |
Tools |
Outcomes |
|---|---|---|
Configuration & Vulnerability Management Services |
Configuration Assessment Vulnerability Assessment |
Limit : Surface Area |
Security Assurance Root Cause Identification |
Compensatory Controls Cyber Range SOAR |
Minimize : Exposure |
24x7 Monitoring Threat Hunting Correlation |
SIEM/XDR Cyber Range |
Reduce : Mean time to Detect |
Heatmap Risk Correlation |
Scoring Tools |
Quantify : Gaps & Actions |
Incident Response |
SOAR/XDR |
Prioritize : Response |
Reporting |
SIEM/XDR Native Reporting Consoles |
Report : Metrics & Compliance |
Explore Use-Cases
For BFSI Businesses
Protection For Brand, Reputation and Revenue
- Respond to phishing attacks
- Detect third party compromise in real-time
- Investigate insider threats as they emerge
- Ensure Compliance with regulatory mandates
CHALLENGES
Cyber threats are 300 times as likely to target the broader financial services industry as companies in other sectors, according to BCG. Whether attackers are attempting to access financial information, take over customer identities, commit fraud, or hold critical files for ransom, your information security team has more than its fair share of challenges.
KEY BENEFITS
- Protect customer, employee, and third -party data
- Prevents financial losses and mitigates the risk
- Avoid penalties for non-compliance with PCI-DSS and other mandates
- Preserve your organization’s reputation
For Healthcare Businesses
Proactive Cyber Defenses to Safeguard Lives
- Ransomware Protection
- Healthcare Provider & Consumer Fraud
- Privileged Access Abuse
- Patient Privacy Protection
- Medical Device Discovery & Monitoring
- Regulatory Compliance
CHALLENGES
Healthcare organizations have some of the most challenging environments to secure. They have geographically dispersed clinical locations, large amounts of sensitive patient and financial data, a range of transitory mobile devices and users, connected life-saving medical devices (known as the Internet of Medical Things, or IoMT), and numerous healthcare applications and systems.
KEY BENEFITS
- Prevent patient record “snooping” – viewing medical records of friends, family, neighbors
- Detect and stop sensitive data exfiltration to personal ids, competition or bad actors
- Protect medical records
- Block unauthorized access to patient data from unrelated departments (e.g. pediatrics nurse accessing records from neurology)
- Detect access to information systems and medical devices from suspicious devices, users and network IP addresses
For Retail Businesses
Detect Fraudulent Behavior and Transactions
- Ransomware Protection
- Credit Card & Online Payment Fraud
- Insider Threat Detection & Deterrence
- PCI – DSS Compliance
CHALLENGES
Every global business in the retail sector face serious cyberthreats. Whether it’s via malware on POS terminals, a hack on a web application, or some other type of attack, retailers risk exposing customer payment data. It’s the most-sought-after and lucrative commodity that threat actors want because it can be monetized quickly and easily. Retailers need to balance the demands of fully securing their environment and data with PCI DSS compliance requirements.
KEY BENEFITS
- Detect and prevent POS fraud
- Identify credit card skimming
- Eliminate online payment fraud
- Curtail call center fraud
For Manufacturing Businesses
Protection Against Cyber Attacks & Data Exfiltration
- Data Exfiltration
- IP Protection
- IOT Analytics / Device Compromise
- Vendor / Partner Account Compromise
CHALLENGES
Cyber threats are 300 times as likely to target the broader financial services industry as companies in other sectors, according to BCG. Whether attackers are attempting to access financial information, take over customer identities, commit fraud, or hold critical files for ransom, your information security team has more than its fair share of challenges in cybersecurity management.
KEY BENEFITS
- Detect APT attacks and attack vectors and predict data exfiltration by performing entity centric anomaly detection.
- Provide risk-based dashboard for closely monitoring high-risk entities and investigation using detailed anomaly timeline based on users, accounts, alerts, and activities associated with the entity.
- Support customized and unique DLP and data classifications, metadata model and big data infrastructure.
Transform Security Operations & Maximize ROI
Numerous alerts and false positives from multiple tools are making it challenging to detect and respond to threats. Lack of cybersecurity talent is making it worse. There is also an explosion of attack vectors, and the threat actors have refined their methods, leveraging machine learning and automation to multiply the threat vectors and intensity; thus, the number and impacts of attacks are only likely to grow from here. It’s high time to adopt a managed Security Operations Centre (SOC) with 24x7 monitoring, remediation, and management capabilities.
