Security Information and Event Management (SIEM)
Enhancing Cybersecurity with Advanced Monitoring and Response
Introduction to SIEM
Security Information and Event Management (SIEM) is an integral component of modern cybersecurity frameworks, designed to provide comprehensive insights through the aggregation and analysis of security data across an organization’s IT environment. By centralizing the data from multiple sources—such as network devices, servers, and applications—SIEM systems offer a holistic view of an organization’s security posture.
Core Capabilities of SIEM
Data Aggregation : SIEM solutions integrate security data from a wide array of sources, creating a centralized platform for security monitoring and management.
Event Correlation : SIEM systems excel in correlating events and logs across the network, identifying patterns that signify potential security incidents.
Alerting and Real-time Analysis : Automated alerting capabilities ensure that any anomalous behavior triggers an immediate response, facilitating rapid decision-making.
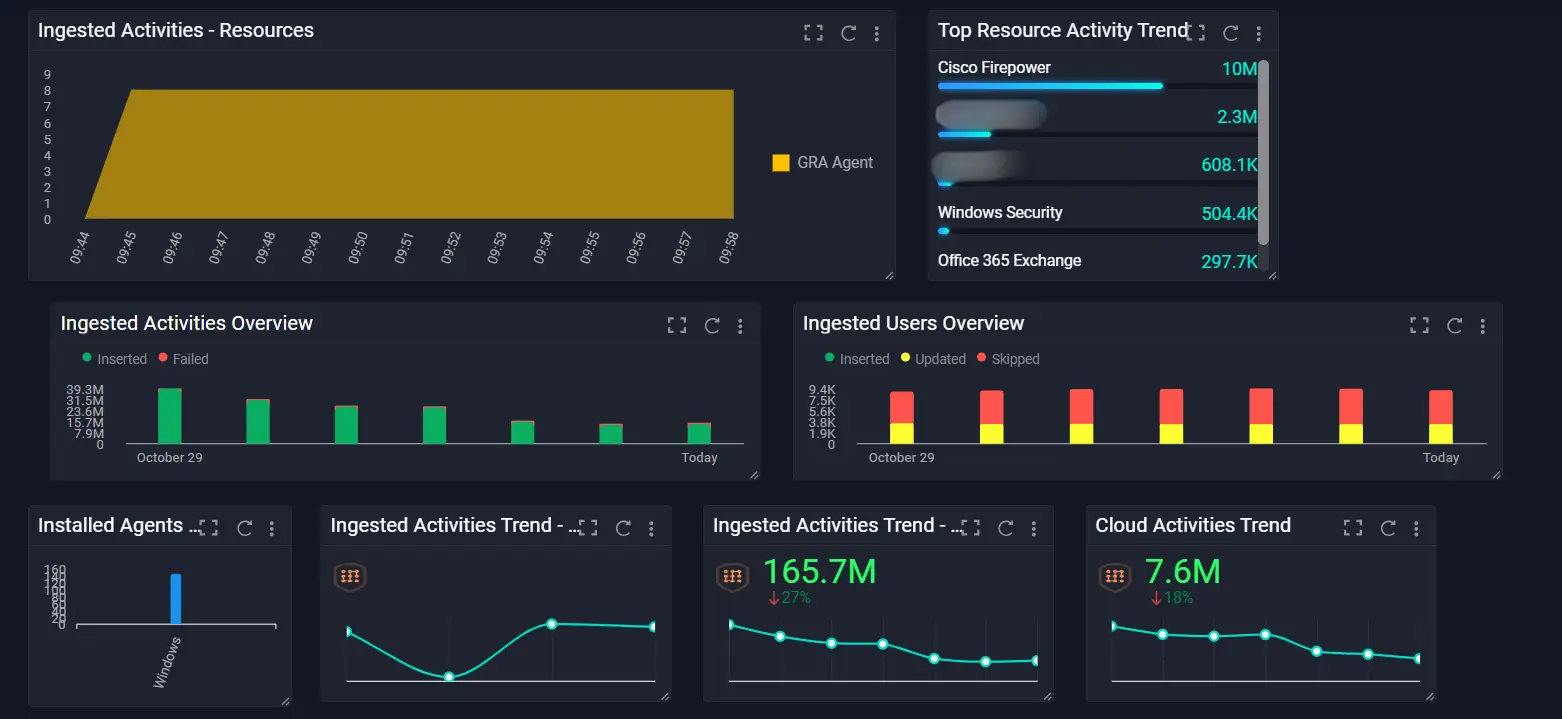
Forensics and Analysis : Extensive logging capabilities of SIEM enable deep forensic analysis, crucial for uncovering the root cause of security incidents and preventing future occurrences.
Our Partners




Expanded Benefits of SIEM
Proactive Threat Detection
By continuously monitoring and analyzing security data, SIEM helps organizations stay ahead of threats by identifying potential security incidents before they cause harm.
Streamlined Compliance
SIEM tools simplify the process of adhering to regulatory requirements with automated log collection and compliance reporting features.
Operational Efficiency
Automation of data collection and analysis not only improves security but also enhances operational efficiency by reducing the manual workload on security teams.

Use Cases for SIEM
Advanced Threat Detection : In industries such as finance and healthcare, where data breaches can have catastrophic consequences, SIEM’s ability to quickly detect and respond to sophisticated threats like zero-day exploits and advanced persistent threats (APTs) is invaluable.
Insider Threat Identification : For organizations that handle sensitive data, SIEM can identify suspicious activities that might indicate insider threats, such as unusual access patterns or large data transfers happening at odd hours.
Efficient Incident Response : In IT and telecommunications, rapid response to incidents is crucial. SIEM facilitates this by integrating with incident response platforms to automate the containment and mitigation processes.
Compliance and Auditing : For sectors under strict regulatory scrutiny, such as public sector and utilities, SIEM supports compliance with standards like GDPR, HIPAA, and SOX by providing comprehensive logs, real-time monitoring, and detailed reports.
